[Profile] ScamClub
Overview: ScamClub is a threat actor known for conducting large-scale scams and defrauding individuals. This group exploits vulnerabilities in the programmatic ad system to carry out forced redirect campaigns.
ScamClub utilizes RTB integration with ad exchanges to push bid responses upstream containing malicious javascript. This code will attempt to redirect victims' web browsers to a malicious landing page without any action or intent on the part of the victims. Forced redirect attacks are harmful because ad recipients can encounter fraudulent landing pages designed to deceive and exploit them. Attacks from ScamClub lead victims to financial scams, gift card scams, phishing pages designed to steal user information, and more. These attacks not only harm ad recipients, they harm websites by damaging their reputation, while also undermining the trust and credibility of DSPs and SSPs, potentially leading to financial losses and strained relationships with advertisers and publishers.
ScamClub uses many techniques to ensure an effective campaign. In June 2020, Confiant observed ScamClub use a zero-day exploit that bypassed a security feature in the ad iframe. This security feature is used to prevent any redirection unless there is a proper click inside of the ad. The exploit bypassed this feature and took the ad recipient away from the page without clicking on the ad.
ScamClub has also been using what we deem high risk ad exchanges. The result of ScamClub using high risk ad exchanges to post their creatives has had a huge negative impact on publishers.
In 2018, when referring to ScamClub campaigns, we found 57% of our publisher clients working with this ad exchange were impacted. The ad exchange ScamClub used at that time was one we deemed high risk. Confiant monitored the delivery of this malvertising campaign, recorded and blocked over 5 million hits in 48 hours. The total amount of impressions served to publishers left without Confiant's protection was estimated at over 300 million impressions during this 48-hour period. By comparison, the Zirconium group was responsible for only one billion impressions throughout the whole year in 2017.
ScamClub Diamond Model Attributes
Using the diamond model of attribution, Confiant threat intelligence determined that on-going malvertising activity impacting multiple ad exchanges, DSPs, SSPs and publishers are attributed to the ScamClub threat actor with high confidence.
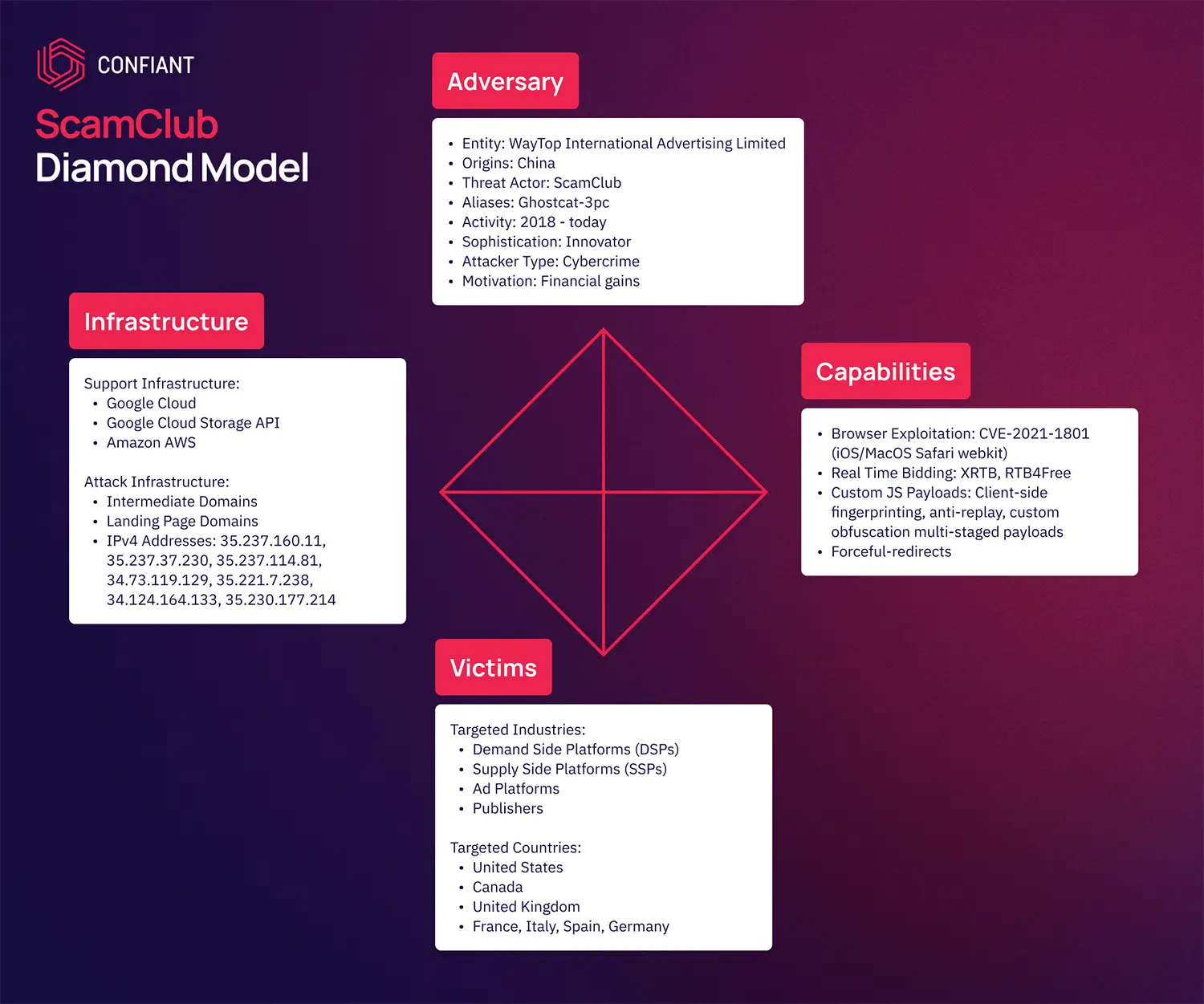
Diamond Model Analysis
| Country of Origin | China |
|---|---|
| Related Entity | WayTop International Advertising Limited |
| Years of Activity | 2018-today |
| Motivation | Financial gains |
| Victimology | This threat actor predominantly targets victims in the United States, with additional victims in Canada, United Kingdom, Germany, Italy, France, and Spain |
| Affected Industries | Advertising |
| Affected Segments | Ad Exchanges, Demand Side Platforms, Supply Side Platforms, Publishers |
| Unique Tools |
→ Multi-staged custom JavaScript obfuscation tool → Browser exploit: CVE-2021-1801 (Safari iOS/MacOS Webkit) |
| Generic Tools | XRTB, RTB4Free |
| Known Infrastructure |
Domain Names: 2020workaffnew[.]top, trkmyclk[.]xyz IPv4 Addresses: 34.73.119.129 34.124.146.133 35.221.7.238 35.230.177.214 35.237.160.11 35.237.37.230 35.237.114.81 ASNs: GOOGLE-CLOUD |
Note: The Diamond Model analysis provides crucial insights into cyber threats, focusing on the who, what, when, where, why, and how aspects of the threat actor and their activities.
Tactics, Techniques, and Procedures (TTPs)
Since the emergence of ScamClub in 2018, Confiant has diligently monitored and recorded the tactics, techniques, and procedures (TTPs) employed by this threat actor based on the comprehensive Confiant Malvertising Matrix model. The creation of this model involved continuous tracking and analysis of 25 distinct threat actors who specifically target the advertising industry. It serves as a vital tool in profiling threat actors and plays a central role in our established cyber threat intelligence program.
Note: We strongly encourage our peers in the ad-tech industry to adopt this model, as it greatly enhances our capabilities in detection and attribution.
Further information on utilizing this model can be found here.
| Confiant Matrix ID | Description |
|---|---|
[C101] |
Fake Advertising Agency is an advertising agency that is owned by malicious operator for the purpose of establishing relationships with ad buying platforms (DSPs). |
[C103] |
Fake ad creative are display advertisements that are typically shown in standalone slots on websites and mobile apps, it is a great entry point for malvertisers. |
[C204] |
Forceful redirects are the technique by which malvertisers redirect victims to a malicious landing page through no action of their own. |
[C301] |
Buckets are cloud containers that store user data. Often used to store and protect any amount of data for websites, mobiles apps for backup and restore. |
[C403] |
Iframe Sandbox bypass are exploits that circumvent iframe sandbox attribute parameters, typically the "allow-top-navigation-by-user-activation" parameter. |
[C601] |
WebGL APIs are heavily leveraged for device fingerprinting, because a device's graphics cards and their performance are highly variable and produce outputs that are in an entropy sweet spot. |
[C602] |
User-Agent Fingerprinting is a client-side check by which adversaries determine Browser types and versions they might potentially be attacking. |
[C603] |
GeoIP is commonly used as a server-side check consisting of determining the geographical location of a potential target based on the IP address. |
[C604] |
IP targeting is a more fine-grained check than GeoIP check, consisting of determining if targets are using their home, datacenter, Enterprise, or 4G mobile connection. |
[C606] |
OS Fingerprinting is a check used to accurately determine the Operating system and its version of a target user. |
[C609] |
Fake AD creatives are copy/pasted legitimate AD creatives that are used by malvertisers as a pretext for them to appear legitimate in the eyes of ad platforms. |
[C612] |
Browser Objects are any objects that are native to a browser's implementation of JavaScript and/or the many APIs available to browsers. |
[C615] |
The Browser Identification through Plugin Detection technique is employed by attackers to determine the type of browser a user is running based on the identified plugins. By leveraging the plugin's API, malicious websites can extract version information of installed plugins on the victim's system. |
[C701] |
Code Obfuscation applies to a broad category of techniques and tactics that are employed by attackers in order to make their code hard to read by human analysts. |
[C703] |
Anti-Devtools techniques are employed by attackers in order to disrupt the debugging process of the malicious code when browser dev tools are detected. |
[C704] |
String Concatenation is an obfuscation technique where strings are split into small chunks and added together so that the original strings will be difficult to search for during static analysis. |
[C705] |
The Document Object Model (DOM) is a standard convention for accessing and manipulating elements within HTML and XML documents. |
[C715] |
Malvertising security vendors typically have a client-side component for blocking malvertisements. |
[C717] |
The Automated Framework Detection Avoidance technique is employed by attackers to identify and differentiate victims using automated testing frameworks, such as Selenium, while attempting to avoid detection and analysis. Attackers achieve this by utilizing JavaScript-based fingerprinting code within malicious websites or applications. |
[C718] |
The anti-replay technique aims to ensure that the malvertising payload is executed only once on a targeted device. |
[C801] |
Gift Card Scams are landing pages that tell the victim they have won an e-commerce gift card, usually to a major retailer. In order to claim the gift card the victim has to fill out a form with their email address or other contact information. |
[C802] |
Carrier Branded Scams are landing pages where the victim is presented with a fake message from their local ISP. |
[C811] |
We generalize these landing pages as Free iPhone Scams, but they often include a multitude of other products or product giveaways including tablets, computers, and other electronics or highend items. |
[C820] |
This technique involves leveraging scare tactics to manipulate victims; a landing page is designed to instill fear in the users by falsely indicating that their system is infected with malware. |
[C904] |
Financial Loss encompasses any attack whose impact results in lost money from the victim targeted by malvertisers. |
Read the full report here:
